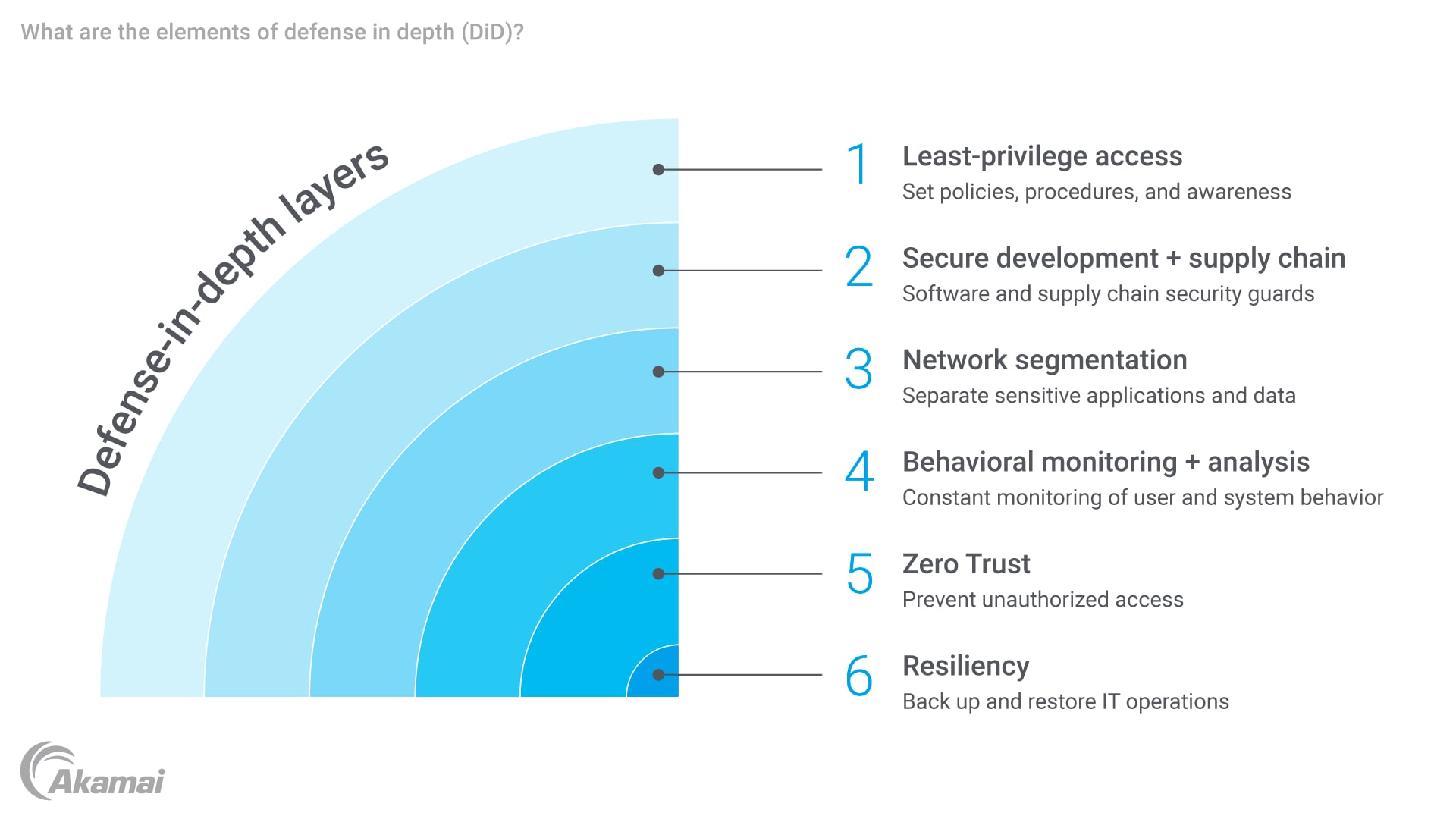
Defense in depth (DiD) provides several advantages for businesses. It enhances resilience by diversifying security measures, ensuring that if one layer is breached, others remain intact. Additionally, DiD improves detection capabilities by increasing visibility across the environment, enabling timely identification of suspicious activities.
Defense in depth aligns with regulatory and compliance requirements, such as GDPR and PCI DSS, by implementing robust security controls. Adhering to these standards mitigates legal and financial risks and fosters trust among customers and stakeholders. Overall, defense in depth offers a comprehensive and effective approach to security.