Explore the benefits of microsegmentation
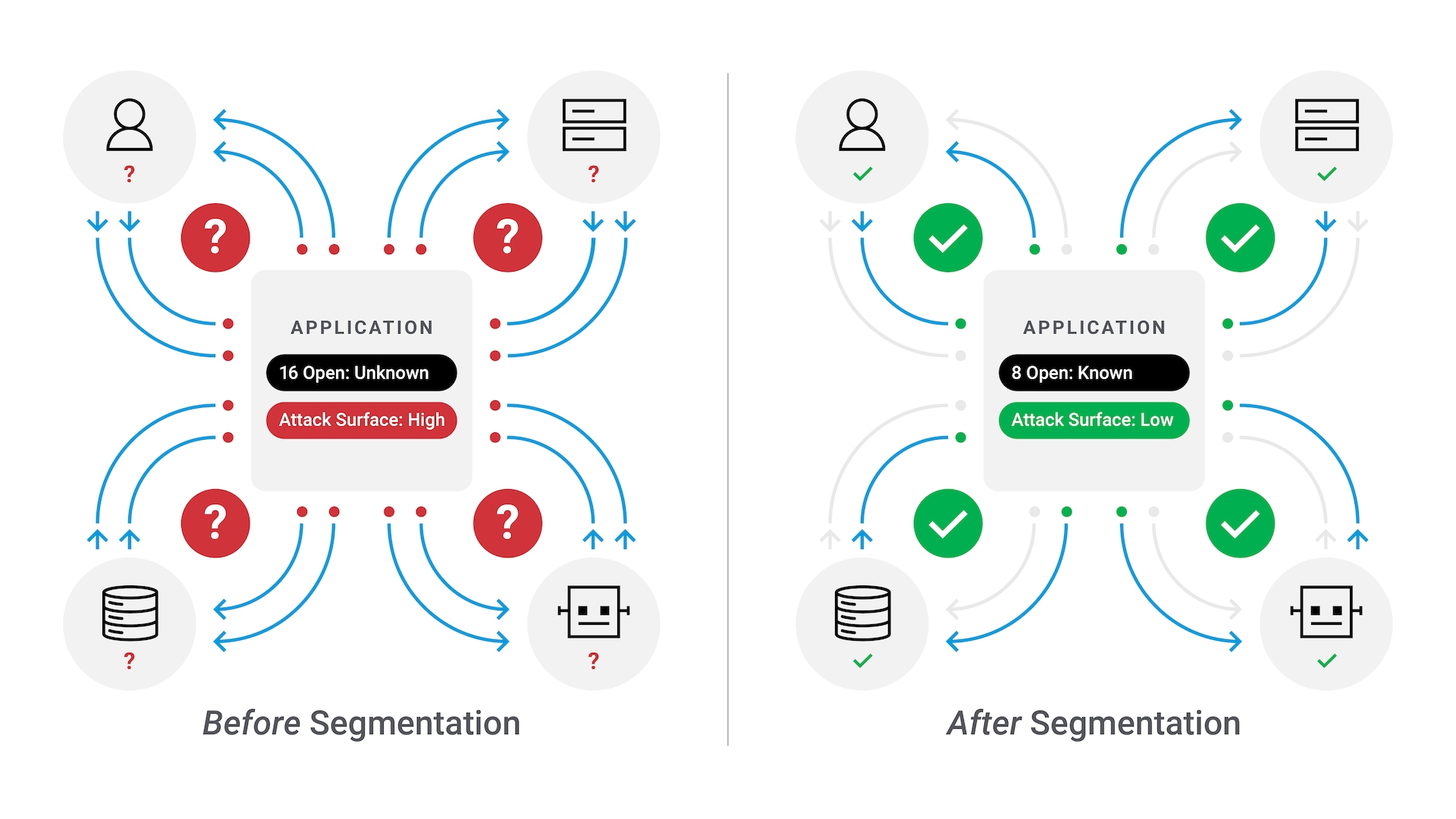
Protect critical assets across your entire environment with Akamai Guardicore Segmentation, the simplest, fastest, most intuitive way to enforce Zero Trust principles.
Easily deploy and manage precise segmentation policies that provide unparalleled visibility while preventing malicious lateral movement in your network.
Explore the benefits of microsegmentation
Akamai Guardicore Segmentation allows you to contain attacks on applications and workloads in hybrid cloud and K8s environments, with the same visibility and policy controls provisioned in on-prem environments. Map your assets and flows across environments, virtual machines, servers, and containers, all from a single pane of glass.
Go beyond the data center to secure Azure, AWS, GCP, and other cloud infrastructure with a single view of the cloud and a single, consistent security policy across your hybrid environment. This allows you to identify threats, anomalies, and potential vulnerabilities while quickly applying security controls that adapt to any change in your cloud environment.
Benefits
Ransomware, like most malware, relies on lateral movement throughout the network to succeed. Many solutions that claim to protect against ransomware focus their efforts on the perimeter, which is fine until a breach inevitably occurs. Without a proper segmentation solution in place, the scope of the breach can be tremendous. Akamai helps businesses remediate and protect against the effects of ransomware by visualizing all assets that are communicating in your environment, quickly implementing policy to limit communications with the infected assets, and securing ransomware recovery efforts.
Benefits:
Many compliance mandates require organizations to segment sensitive or critical data from the rest of their IT infrastructure. Software-based segmentation makes this process easier, but many solutions do not provide comprehensive visibility into the network, making it more challenging and time-consuming to complete these segmentation projects and validate compliance. Akamai helps businesses accelerate and validate data compliance initiatives by providing a single source of truth for what’s communicating within your network and enabling consistent policy enforcement across IT infrastructures. This simplifies identifying assets in scope, segmenting those assets from the rest of your IT environment, and validating your compliance with real-time and historical views.
Benefits:
Most organizations have a select set of applications that are the lifeblood of their business, from customer-facing web applications to databases containing valuable or sensitive information. Security incidents affecting these types of critical assets can have a significant impact on a company’s business and reputation. Akamai helps security teams give critical applications the security focus they require by providing a visual map of how they work, making it easy to ringfence them with precise segmentation policies, and protectively detecting targeted attacks.
Benefits:
A solid foundation for workload protection and compliance is the granular isolation and segmentation of your network applications and their components. Akamai Guardicore Segmentation enables deep application dependencies mapping and policy enforcement, ensuring an ongoing management process of your microsegmentation policy. It delivers one of the industry’s most complete and flexible solutions for microsegmentation, featuring the following key attributes:
Benefits:
Securing IoT and OT devices has traditionally been a challenge for most organizations. With Akamai Guardicore Segmentation, organizations are now able to reduce their attack surface and enforce Zero Trust policies on devices that can’t run host-based security software. Major features include:
Benefits:
Yes, you can run your firewalls in parallel with Akamai’s microsegmentation solution. However, Akamai Guardicore Segmentation is a more granular and flexible network segmentation solution that should enable you to remove most of your firewalls, especially your internal ones. Many clients run them in parallel for a short period of time until they are comfortable with the new policy enforcement.
It includes both agent-based and agentless options. This flexibility ensures that security and segmentation can be enforced across a wide range of environments. Deploying agents is recommended for achieving maximum visibility and control over network traffic and activities. Agentless is ideal for in-cloud PaaS, IoT, and OT environments.
Policy creation is fast and easy. Using AI, our microsegmentation solution suggests policies through intuitive templates and workflows, and allows you to customize them based on your own business needs.
It is a stand-alone microsegmentation product that protects east-west traffic and enforces one of the core principles of Zero Trust, as defined by both Forrester® and Gartner®. Forrester states that “Microsegmentation Is Essential For Zero Trust Private Networks” in its 2022 Forrester New Wave™.
Akamai provides managed threat hunting services through Akamai Hunt, which finds and remediates the most evasive network security risks in your environment. It is led by security experts from Akamai’s threat intelligence and analytics teams — and utilizes the data gathered from the Akamai Guardicore Segmentation solution — to search for threats in your network, find and virtually patch vulnerabilities, and harden your infrastructure.

Akamai Guardicore Segmentation gives you better visibility to control and stop the spread.
Get real-time visibility and powerful control against lateral movement. See how Akamai Guardicore Segmentation helps you protect your network and stay ahead of attacks. Request your demo today.
Schedule your demo in two easy steps:
An Akamai expert will reach out soon.
1GARTNER® is a registered trademark and service mark, and PEER INSIGHTS™ is a registered trademark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and are used herein with permission. All rights reserved. Gartner Peer Insights content consists of the opinions of individual end users based on their own experiences, and should not be construed as statements of fact, nor do they represent the views of Gartner or its affiliates. Gartner does not endorse any vendor, product or service depicted in this content nor makes any warranties, expressed or implied, with respect to this content, about its accuracy or completeness, including any warranties of merchantability or fitness for a particular purpose.