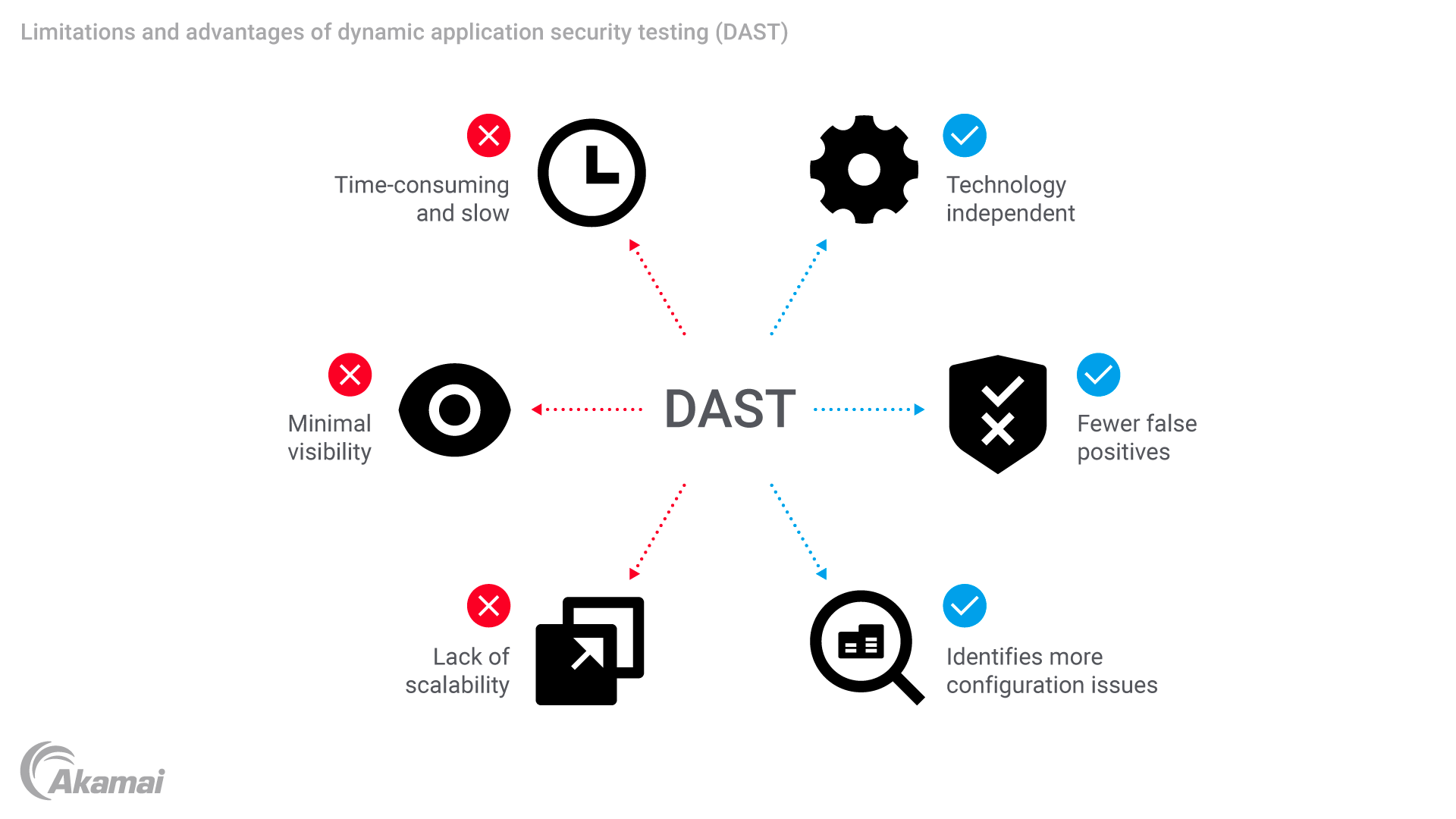
Dynamic application security testing (DAST) is essential for web application security due to its unique capabilities. DAST helps identify runtime vulnerabilities by simulating real-world hacking attempts. By actively scanning applications during runtime, DAST tools uncover vulnerabilities that may evade traditional static analysis.
This approach provides a comprehensive understanding of the application’s security position, enabling organizations to address vulnerabilities before malicious actors can exploit them. Incorporating DAST into security testing strategies enhances cybersecurity by fortifying web applications against cyberattacks and ensuring robust protection for sensitive data and assets.