The best protection against DoS attacks and DDoS attacks is a multilayered posture that can protect websites, applications, APIs, authoritative DNS, and network resources by using technologies that have a proven record for blocking these events.
In a distributed denial-of-service (DDoS) attack, a type of cyberattack, an attacker overwhelms a website, server, or network resource with malicious traffic. As a result, the target crashes or is unable to operate, denying service to legitimate users and preventing legitimate traffic from arriving at its destination.
From a high level, a DDoS or DoS attack is like an unexpected traffic jam caused by hundreds of bogus rideshare requests. The requests appear to be legitimate to rideshare services, and they dispatch drivers for pickup that inevitably clog up the city streets. This prevents regular legitimate traffic from arriving at its destination.
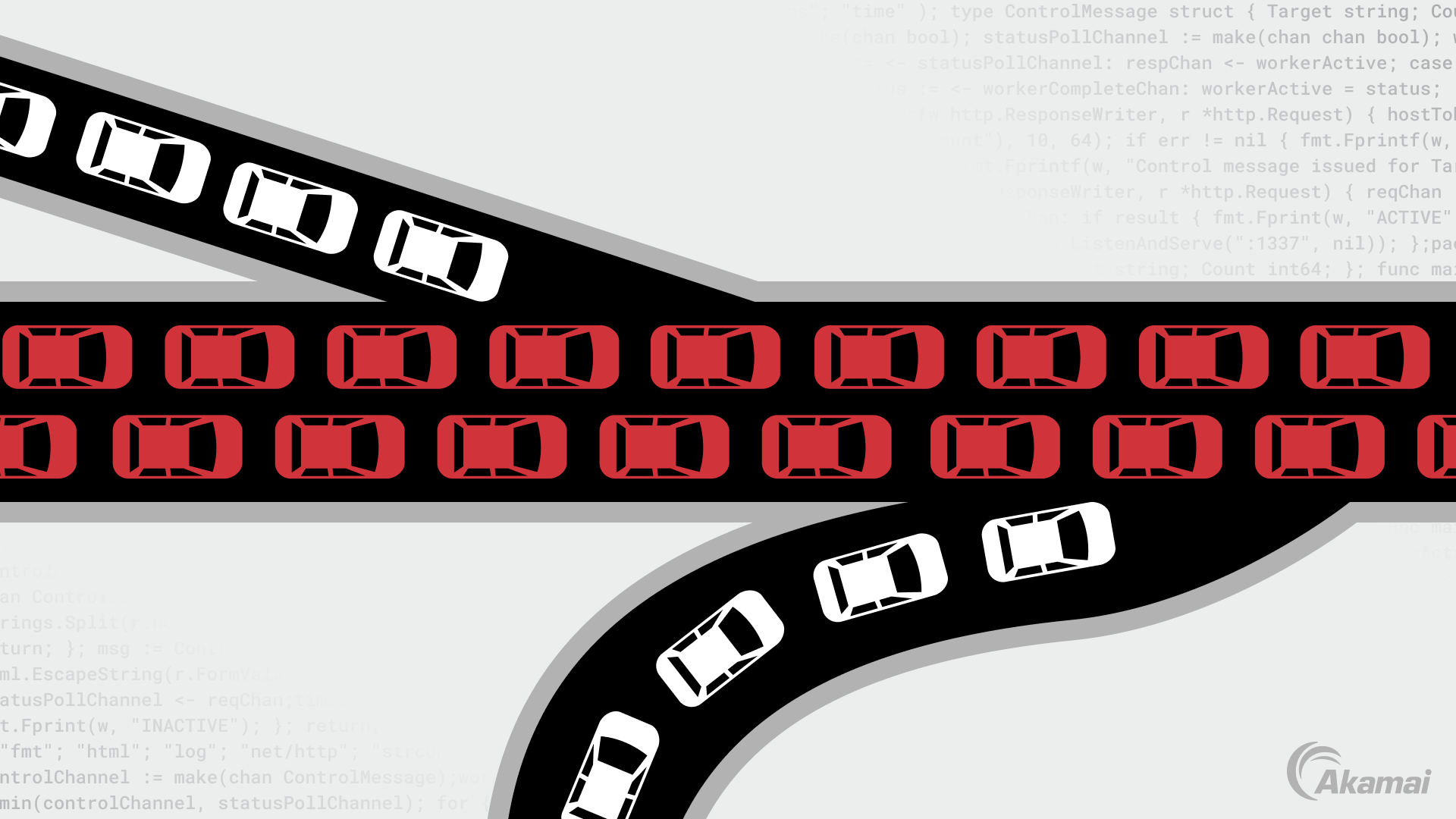
A DDoS attack on a company’s website, web application, APIs, network, or data center infrastructure can cause downtime and prevent legitimate users from buying products, using services, getting information, or accessing other resources.
Building a botnet — To launch a DDoS attack, attackers use malware to create a network of bots — internet-connected devices that are infected with malware, which attackers can direct to send a flood of traffic to targets. This bot network, or botnet, may include endpoints like Internet of Things (IoT devices), smartphones, and personal computers, as well as routers and network servers. Each infected device becomes capable of spreading the malware to other devices to amplify the size of an attack.
To use a popular culture reference here, think of how the Night King in the HBO series Game of Thrones created an army of White Walkers. The Night King created an initial set of White Walkers. These White Walkers attacked humans to turn them into new White Walkers, and thus the army kept growing. And every single member of this army was controlled by the Night King.
Launching an attack — Once an attacker has built a botnet, they send remote instructions to the bots, directing them to send requests and traffic to a targeted server, website, web application, API, or network resource. This creates an overwhelming amount of traffic that leads to a denial of service, preventing normal traffic from accessing the target.
DDoS as a service — Sometimes botnets, with their networks of compromised devices, are rented out for other potential attacks through “attack-for-hire” services. This allows people with malicious intent but no training or experience to easily launch DDoS attacks on their own.
The purpose of DDoS attacks is to severely slow down or stop legitimate traffic from reaching its intended destination. For example, this could mean stopping a user from accessing a website, buying a product or service, watching a video, or interacting on social media. Additionally, by making resources unavailable or diminishing performance, DDoS can cause business to grind to a halt. This can result in preventing employees from accessing email or web applications, or conducting business as usual.
DDoS attacks may be launched for several reasons.
There are many different types of DDoS attacks, and cybercriminals often use more than one type to take down their targets. DDoS attacks typically target one of the seven different layers of a computer network as described in the Open Systems Interconnection (OSI) model. Each layer of the OSI model has a unique purpose, like the floors of an office building where different functions of a business take place on each floor. Attackers target different layers depending on what type of web or internet-facing asset they’d like to disrupt.
The four key types of attacks are:
Application-layer DDoS attacks (Layer 7 DDoS attacks) target specific vulnerabilities in web applications to prevent the application from performing as intended. These DDoS attacks often target the communication protocols involved in exchanging data between two applications over the internet. While difficult to prevent and mitigate, they are among the easiest DDoS attacks to launch.
Protocol attacks target weaknesses and vulnerabilities in internet communications protocols in Layer 3 and Layer 4 of the OSI model. These attacks attempt to consume and exhaust compute capacity of various network infrastructure resources like servers or firewalls by sending malicious connection requests that exploit Transmission Control Protocol (TCP) or Internet Control Message Protocol (ICMP) protocols.
Domain Name System or DNS amplification/reflection attacks are a specific type of volumetric DDoS attack vector where hackers spoof the IP address of their target to send large amounts of requests to open DNS servers. In response, these DNS servers respond back to the malicious requests by the spoofed IP address, thereby creating an attack on the intended target through a flood of DNS replies. Very quickly, the large volume of traffic created from the DNS replies overwhelms the victim organization’s services, making them unavailable and preventing legitimate traffic from reaching its intended destination.
To explain this type of attack using the rideshare analogy, imagine if hundreds or thousands of rideshare requests were placed to send cabs to a victim’s address. These rideshare cabs now clog up the streets leading up to the victim’s house, preventing legitimate visitors from reaching the individual’s address. This analogy can also be extended to explain volumetric DDoS attacks in the next section.
Volume-based DDoS attacks are directed at OSI Layers 3 and 4, overwhelming a target with a flood of traffic from multiple sources and eventually consuming all of the target’s available bandwidth, causing it to slow down or crash. Volumetric attacks are often used to divert attention away from other types of DDoS attacks or more dangerous cyberattacks.
Organizations can protect against and limit disruption from DDoS attacks with a strong DDoS strategy, superior DDoS mitigation services, and advanced superior cybersecurity controls.
Cloud-based solutions offer high-capacity, high-performance, and always-on anti-DDoS protection that can prevent malicious traffic from reaching a website or interfering with web API communications, limiting the impact of the attack while allowing normal traffic to get through for business as usual.
In a constantly evolving attack landscape, DDoS protection through a mitigation provider that takes a defense-in-depth approach can keep organizations and end users safe. A DDoS mitigation service will detect and block DDoS attacks as quickly as possible, ideally in zero or a few seconds from the time that the attack traffic reaches the mitigation provider’s scrubbing centers. Because attack vectors keep changing and attack sizes keep getting bigger, to achieve the best DDoS protection, a provider must continually invest in defense capacity. To keep up with large, complex attacks, the right technologies are needed to detect malicious traffic and begin robust defensive countermeasures to mitigate attacks quickly.
DDoS mitigation providers filter out attack traffic to prevent it from reaching the intended targeted asset. Attack traffic is blocked by a CDN-based web protection service, a DDoS scrubbing service, or a cloud-based DNS service.
During mitigation, your DDoS protection provider will deploy a sequence of countermeasures aimed at stopping and diminishing the impact of a distributed denial-of-service attack. As modern attacks become more advanced, cloud-based DDoS mitigation protection helps to provide defense-in-depth security at scale, keeping back-end infrastructure and internet-facing services available and performing in an optimal manner.
Through DDoS attack protection services, organizations can:
Akamai provides in-depth DDoS defense and mitigation services through a transparent mesh of dedicated edge, distributed DNS, and cloud scrubbing defenses. These purpose-built cloud services are designed to strengthen DDoS and network security postures while reducing attack surfaces, improving the quality of mitigation and reducing false positives while increasing resiliency against the largest and most complex attacks. Moreover, the solutions can be fine-tuned to the specific requirements of your web applications and internet-based services.
A DoS attack, or denial-of-service attack, is designed to render a website, router, server, or network unavailable to legitimate users. A DoS attack is launched from a single computer, while a distributed denial-of-service (DDoS) attack uses a botnet or distributed network of IPv4 or IPv6 addresses — a robot network of hijacked computers, machines, or IoT devices — to attack a target from multiple locations.
A DoS or DDoS attack attempts to flood a server, website, network device, or machine with so much malicious traffic that it is unable to operate. In a volumetric attack — such as an ICMP flood or a UDP flood attack — attackers overwhelm a target with massive amounts of traffic, overloading the system, or network path to the system, while preventing legitimate traffic and users from accessing that resource.
A protocol attack such as a SYN flood attempts to consume and exhaust the compute capacity of network infrastructure resources like firewalls or load balancers by sending malicious connection requests that exploit protocol communications. In an application-layer attack like Slowloris, attackers exploit the capacity of a web server, application server, or database by exhausting the amount of requests it can handle while flying under the radar of low request volumes, rendering it unavailable to users.
The best protection against DoS attacks and DDoS attacks is a multilayered posture that can protect websites, applications, APIs, authoritative DNS, and network resources by using technologies that have a proven record for blocking these events.
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.
Stop DDoS attacks with the fastest, most effective defense — at scale.
Rely on highly secure DNS for nonstop availability of web apps and APIs.
One-stop, zero-compromise security for websites, applications, and APIs.

All DDoS mitigation is not created equal. See how many cloud service providers fall short, and what to look out for.

Our latest research gives you the knowledge you need to better defend against rising DDoS attacks in EMEA.

DNS is one of the oldest internet infrastructures. However, an incredible amount of attack traffic passes through it. Details about the most prevalent threats and more can be found in this report.
Learn more about related topics and technologies on the pages listed below.