OAuth helps to secure access to protected resources on an API by allowing end users to authorize third-party applications without sharing their credentials. It manages authentication and authorization through secure access tokens, adding a layer of security to API interactions.
OAuth is an important component in securing APIs. It enables users to grant limited access to their resources without revealing their credentials, thereby establishing secure authentication and authorization mechanisms for accessing protected resources. The OAuth 2.0 framework offers a range of enhancements to the original version, including separating the roles of the client application and the resource owner, which enables greater flexibility and scalability.
OAuth (open authorization) is an open standard protocol that allows users to grant limited access to their resources on one website to another website or application without sharing their credentials. It provides a secure and standardized way for users to authorize third-party applications to access their data on various platforms, including social media, cloud services, and other web-based services.
OAuth plays a key role in API security by enabling secure authentication and authorization mechanisms for accessing protected resources. On this page, we’ll discuss how OAuth security works and the role it plays in helping protect application programming interfaces (APIs).
OAuth and API security: An overview
APIs have become the foundation of modern software development, allowing different applications and systems to communicate and share data seamlessly. However, with the growing number of APIs and the sensitive data they handle, ensuring their security has become a critical concern.
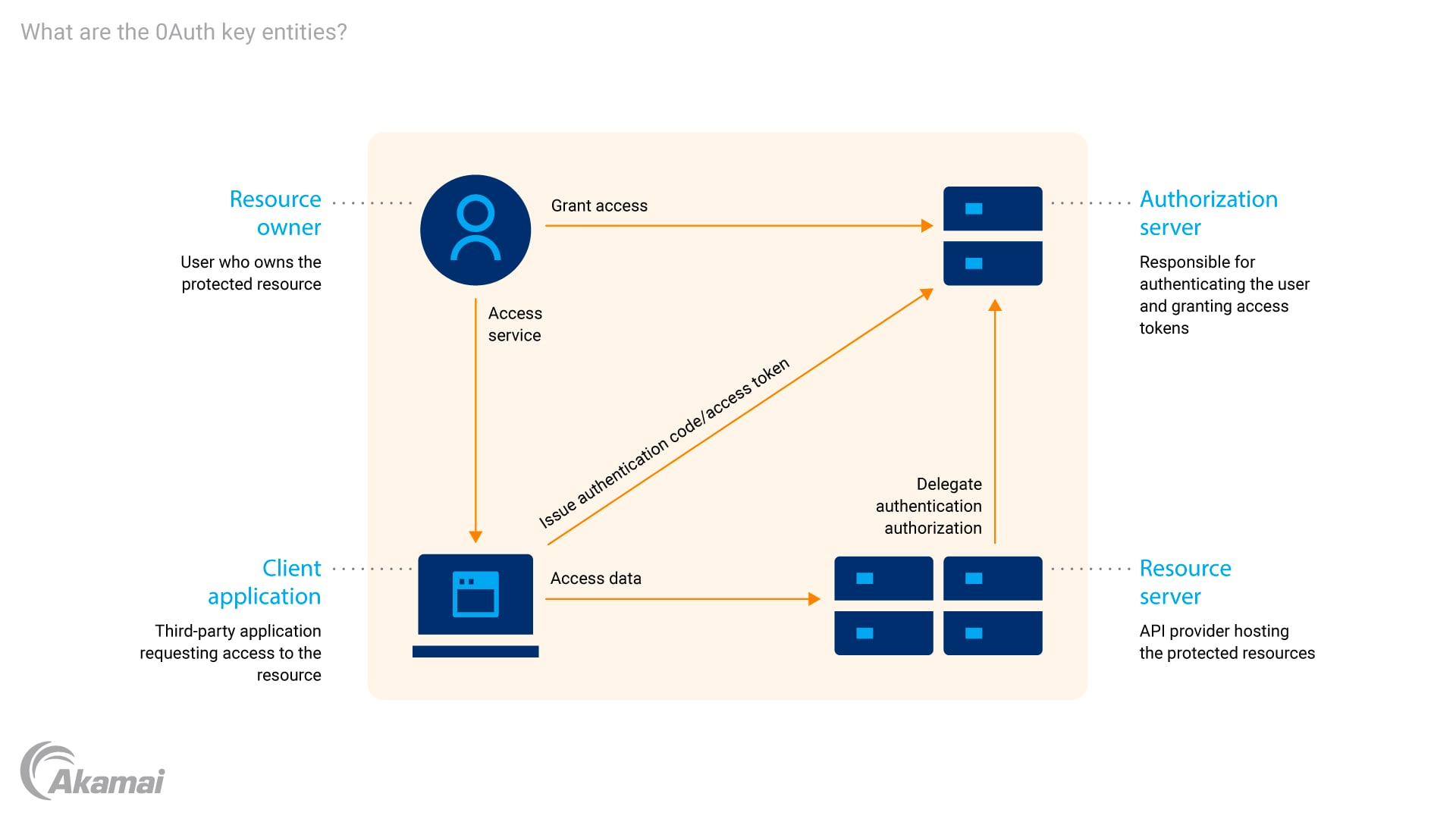
OAuth acts as a framework for granting access to protected resources without exposing user credentials. It allows users to delegate access to their resources to third-party applications, known as clients, through a series of well-defined steps. These steps involve the interaction between the user, the client application, and the API provider, ensuring that only authorized access is granted. The OAuth protocol involves several key entities:
- The resource owner (the user who owns the protected resource)
- The client application (the third-party application requesting access to the resource)
- The authorization server (responsible for authenticating the user and granting access tokens)
- The resource server (the API provider hosting the protected resources)
OAuth and API security: How it works
The OAuth flow typically begins with the client application requesting authorization from the resource owner. This request is usually initiated through a user interface, where the user is presented with the option to grant or deny access to their resources. Once the user grants authorization, the client application receives an authorization grant.
The client application then exchanges this authorization grant with the authorization server for an access token. The access token serves as a credential that the client application can use to access the protected resources for the user. The authorization server verifies the grant and issues the access token, which is then securely stored by the client application.
When the client application needs to access a protected resource, it presents the access token to the resource server. The resource server validates the access token and grants access to the requested resource if the token is valid and the client application has the necessary permissions. This process ensures that only authorized clients can access the protected resources, providing a layer of API security.
OAuth also supports the concept of scopes, which define the specific permissions granted to the client application. Scopes allow fine-grained control over the level of access granted to the client, ensuring that it only has access to the necessary resources and actions.
The OAuth 2.0 framework
OAuth 2.0 is a widely adopted authorization framework that provides a standardized way for users to grant limited access to their resources on one website or application to another website or application without sharing their credentials. It introduces several key improvements over its predecessor, the OAuth 1.0 protocol. The OAuth 2.0 framework:
- Focuses on simplicity, making it easier for developers to understand and implement
- Separates the roles of the client application and the resource owner, allowing for more flexibility and scalability
Introduces the concept of access tokens, which serve as credentials for accessing protected resources
OAuth 2.0 defines several grant types that cater to different use cases and security requirements. These grant types include the authorization code grant, implicit grant, client credentials grant, and resource owner password credentials grant. Each grant type has its own characteristics and is suitable for specific scenarios. The framework also entails the above-mentioned concept of scopes.
OAuth advantages and disadvantages
One of the key benefits of OAuth is its ability to enable secure access to APIs without requiring users to share their credentials with third-party applications. This eliminates the need for users to create separate accounts or share sensitive information, thereby reducing the risk of credential theft or misuse. Additionally, OAuth provides a standardized and widely adopted framework, simplifying the implementation of secure authentication and authorization mechanisms in applications for developers.
However, it’s important to note that OAuth is not a silver bullet for API security. While it addresses authentication and authorization aspects, it does not guarantee the security of the underlying API implementation. API providers must still make sure that their APIs are:
- Designed and implemented securely from the earliest stages
- Visible, accounted for, and assessed for risk via API discovery and posture management
- Continuously tested for misconfigurations and vulnerabilities to attacks
- Protected via runtime security throughout their entire lifecycle
OAuth in web and mobile apps
OAuth provides a secure framework for managing authentication and authorization protocols in mobile and web applications. In a typical web app setup, the application requests user authorization, redirecting to an authorization endpoint where the end user grants access. This authorization request is essential in generating an access token, which the web app uses to access the resource server (for the user). Mobile apps leverage OAuth authorization flows, with security adjustments for app-specific behavior. By using OAuth, developers can protect sensitive user information and streamline login experiences across platforms.
Understanding OAuth endpoints and authorization requests
OAuth utilizes several key endpoints to facilitate secure authorization, including the authorization and token endpoints. During an authorization request, the client app redirects the user to the authorization endpoint, where the end user grants permissions. The authorization server then issues an authorization code or token, depending on the flow used. A JSON-based response is typically returned to the client, containing the access token or any error messages. These endpoint interactions, along with parameters like client ID and scope, enable a secure, streamlined user authentication experience.
Key takeaways: OAuth, APIs, and protecting enterprise data
In conclusion, OAuth plays a key role in API security by providing a standardized framework for secure authentication and authorization. By implementing OAuth, API providers can enhance the security of their APIs and protect user data and a user’s account from unauthorized access. However, it’s important to remember that OAuth is just one piece of the puzzle, and that API providers must still implement robust cybersecurity measures to minimize risk for the overall security of their APIs.
Frequently Asked Questions
OAuth is primarily used for authorization, granting access to resources, while OpenID Connect is an authentication protocol built on top of OAuth 2.0. OpenID Connect verifies the user’s identity, allowing the client app to confirm the end user’s identity through an ID token.
A refresh token is issued along with an access token and allows the client app to obtain a new access token after the original one expires, enabling continued access without requiring the end user to reauthorize.
OAuth uses access tokens to authorize requests to protected endpoints, ensuring that only authorized clients can access the data. The resource server validates tokens, and scopes control the specific permissions granted to each client.
Yes, OAuth is designed to be compatible with various platforms, including web and mobile applications. Different grant types within OAuth 2.0, such as the authorization code and implicit grants, cater to specific scenarios in mobile and web applications.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.