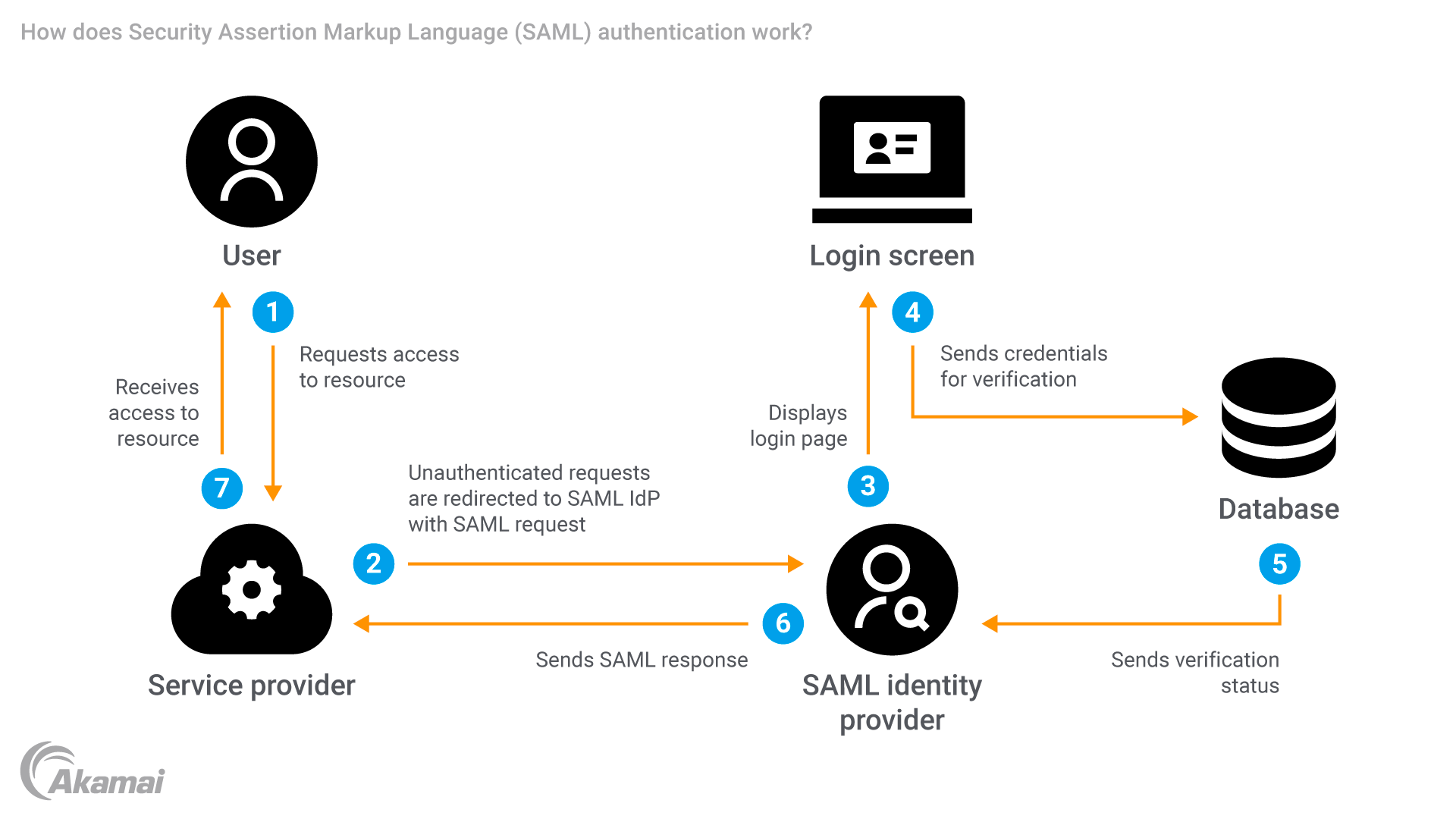
The XML-based protocol, Security Assertion Markup Language (SAML) authentication, enables web browser single sign-on (SSO) capabilities. The process typically occurs through an XML document containing security tokens known as a SAML assertion.
The primary use for SAML is to authenticate a user with an identity provider (IdP) to verify who they are. Using that authentication, the IdP can let the service provider (SP) know it’s okay to grant the user authorized access to multiple secured services or applications using the same credentials.