Network segmentation divides an IT network into several smaller pieces and limits the traffic between them.
Understanding network segmentation
Network segmentation has emerged as an essential security strategy for organizations defending against increasingly sophisticated cyberattacks. By dividing networks into smaller subnetworks and limiting activity between them, network segmentation can significantly reduce your attack surface and minimize damage when an attack successfully breaches perimeter defenses.
Here’s the challenge in designing network segmentation initiatives: They’re difficult to implement at cloud scale and in dynamic infrastructures where workloads are communicating across hybrid environments. Traditional firewalls and other legacy network segmentation tools are of little use here. They’re concerned with controlling north-south traffic between clients and servers rather than the east-west traffic that attackers exploit to move laterally and undetected within an environment.
Akamai Guardicore Segmentation can help. Providing a software-based microsegmentation solution, Akamai delivers the visibility, flexibility, and scalability required for superior network segmentation design. With Akamai, you can quickly and easily visualize and segment assets across your entire IT environment — in the data center, in the cloud, and in hybrid cloud infrastructure.
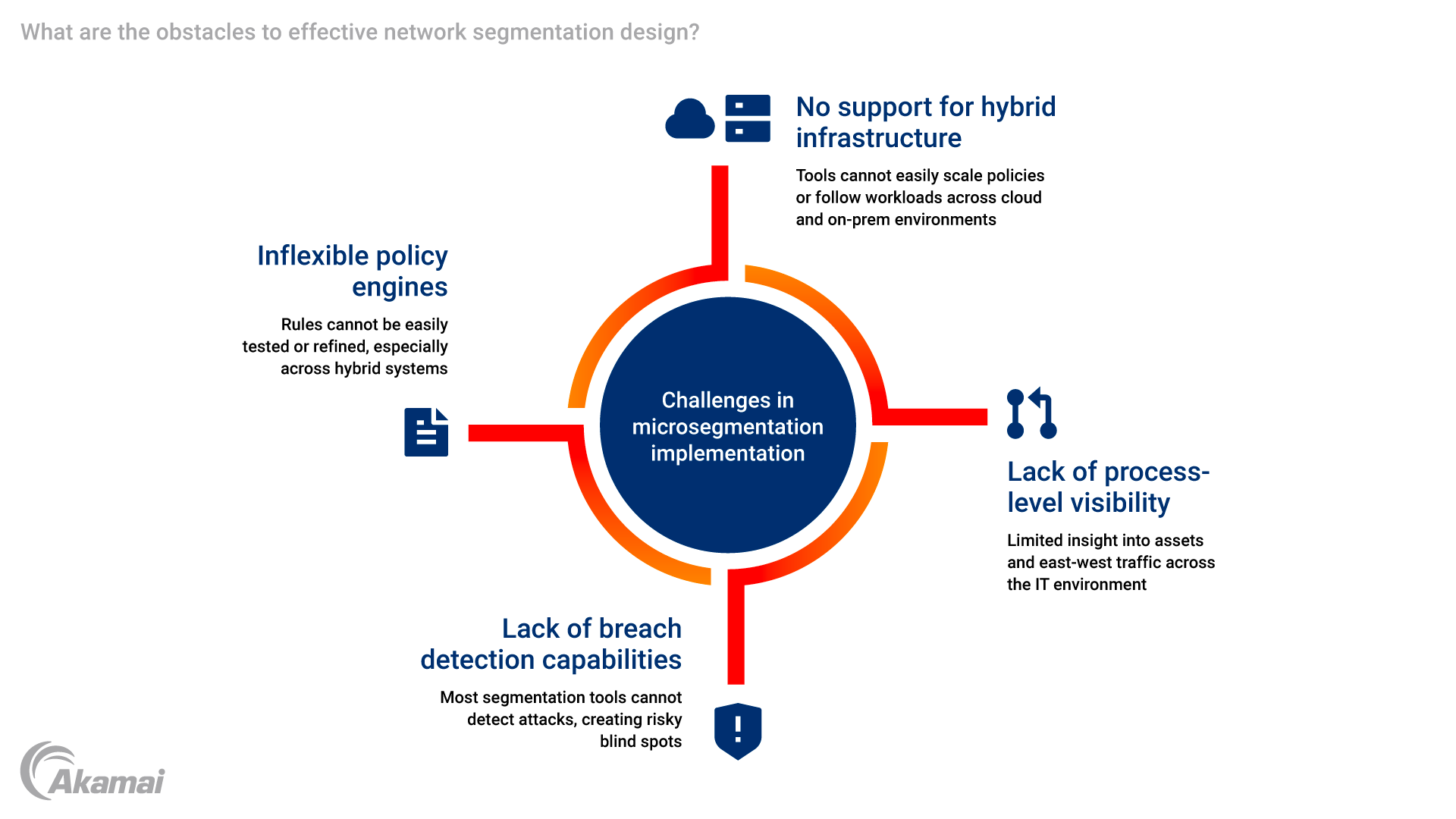
The obstacles to an effective network segmentation design
Microsegmentation is the most effective form of network segmentation when it comes to reducing the risk of lateral spread in advanced attacks. Microsegmentation uses strict network segmentation policy to limit who and what can communicate with individual assets, effectively blocking unauthorized communication and detecting attacks in progress.
Organizations attempting to incorporate microsegmentation techniques in network segmentation design typically run into four main obstacles.
Lack of process-level visibility. Most tools used in network segmentation design can’t provide comprehensive visibility into all the assets within an IT environment or the east-west traffic flows required to understand them in context.
No support for hybrid infrastructure. Many tools for segmentation are designed for specific environments. That makes them ineffective at creating policies that can scale easily across on-premises public cloud environments or follow workloads as they move back and forth.
Inflexible policy engines. Most existing network segmentation firewalls and tools don’t provide the flexibility to constantly scope, test, and refine rules. In a hybrid infrastructure that requires multiple policy tools, this challenge can be compounded exponentially.
Lack of breach detection capabilities. A superior network segmentation design isn’t just about protecting environments but also about detecting attacks. Most single-function segmentation tools don’t include breach detection capabilities. That means security teams must work with a patchwork approach that carries a high risk of failure.
Akamai platform for software-based segmentation
Akamai Guardicore Segmentation is a software-based segmentation solution that dramatically simplifies and improves network segmentation design. With a software-only approach that’s decoupled from the physical network, it provides a faster and more cost-effective alternative to firewalls. Designed specifically for the agile enterprise, Akamai Guardicore Segmentation delivers greater security and visibility anywhere you need it across your entire environment: cloud, data center, and endpoints.
Akamai delivers all the tools you need to design a highly effective microsegmentation network.
Process-level visibility: Akamai Guardicore Segmentation automatically discovers your critical IT assets and lets you visualize dependencies and flows between them with process-level context. This lets your security teams easily label and group all assets and applications to streamline policy development.
A flexible policy engine: With Akamai Guardicore Segmentation, your network segmentation design can include high-level compliance rules for large segments and more granular rules for microsegments. You can quickly build strong policies by simply clicking on a communication flow within Akamai Guardicore Segmentation’s network segmentation diagram and automatically generate suggestions for rules based on historical observations. An intuitive workflow and AI-powered templates make policy creation seamless and automatic.
Streamlined management: Akamai Guardicore Segmentation makes it easy to deploy, maintain, and modify policies as needed. Security teams can enforce communication policies at the network process level on both Windows and Linux systems.
Breach detection capabilities: Akamai Guardicore Segmentation provides additional tools for detecting and blocking threats, including a proprietary threat intelligence firewall, dynamic deception tools, and signature-based reputation analysis.
Benefits of network segmentation design with Akamai
When designing network segmentation with Akamai Guardicore Segmentation, you can:
Prevent lateral movement: Akamai’s microsegmentation capabilities prevent threat actors from moving laterally within an environment, helping to uncover attacks in progress and dramatically reducing the impact of a breach.
Achieve Zero Trust security: Akamai helps you implement Zero Trust security 100% faster by isolating critical applications up to 20x faster than firewalls and by quickly creating and implementing segmentation policies. To reduce risk faster with fewer required rules, Akamai offers a flexible model that includes both application allowlisting and blocking.
Simplify compliance: By enabling a Zero Trust approach to security, Akamai reduces the scope of compliance initiatives such as PCI DSS and SWIFT, lowering costs and minimizing the burden of compliance tasks for IT teams.
Why design network segmentation with Akamai?
A software-based approach: With Akamai, there’s no hardware to be purchased, installed, maintained, and upgraded, allowing you to create network segmentation design more quickly.
Extensive coverage: Akamai protects applications and workloads no matter where they are deployed — on-premises, in the cloud, on virtual servers, on bare metal, or in containers.
No downtime or changes: With Akamai’s software-based approach, you can implement network segmentation design much more quickly, with no changes to networks or applications and no downtime.
Support for legacy systems: Akamai supports legacy operating systems like AS/400, CentOS 6, RHEL 5, and Windows 2003.
Universal policy enforcement: Akamai lets you enforce the same granular, process-level rules across different operating environments, including Windows and Linux.
Frequently Asked Questions
By controlling traffic between different parts of a network, security teams can prevent an attack in one part of the network from reaching other areas. Network segmentation design may also improve operational performance by minimizing network congestion. And teams can reduce the scope of compliance efforts by limiting the size of the network that is subject to regulatory requirements.
Traditional technologies for managing segmentation policies include internal firewalls, access control lists (ACLs), and virtual area local networks (VLANs). However, these approaches tend to be difficult to manage and limited in their effectiveness. Software-defined segmentation tools offer a faster and more cost-effective alternative for managing segmentation policy and monitoring network traffic.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.