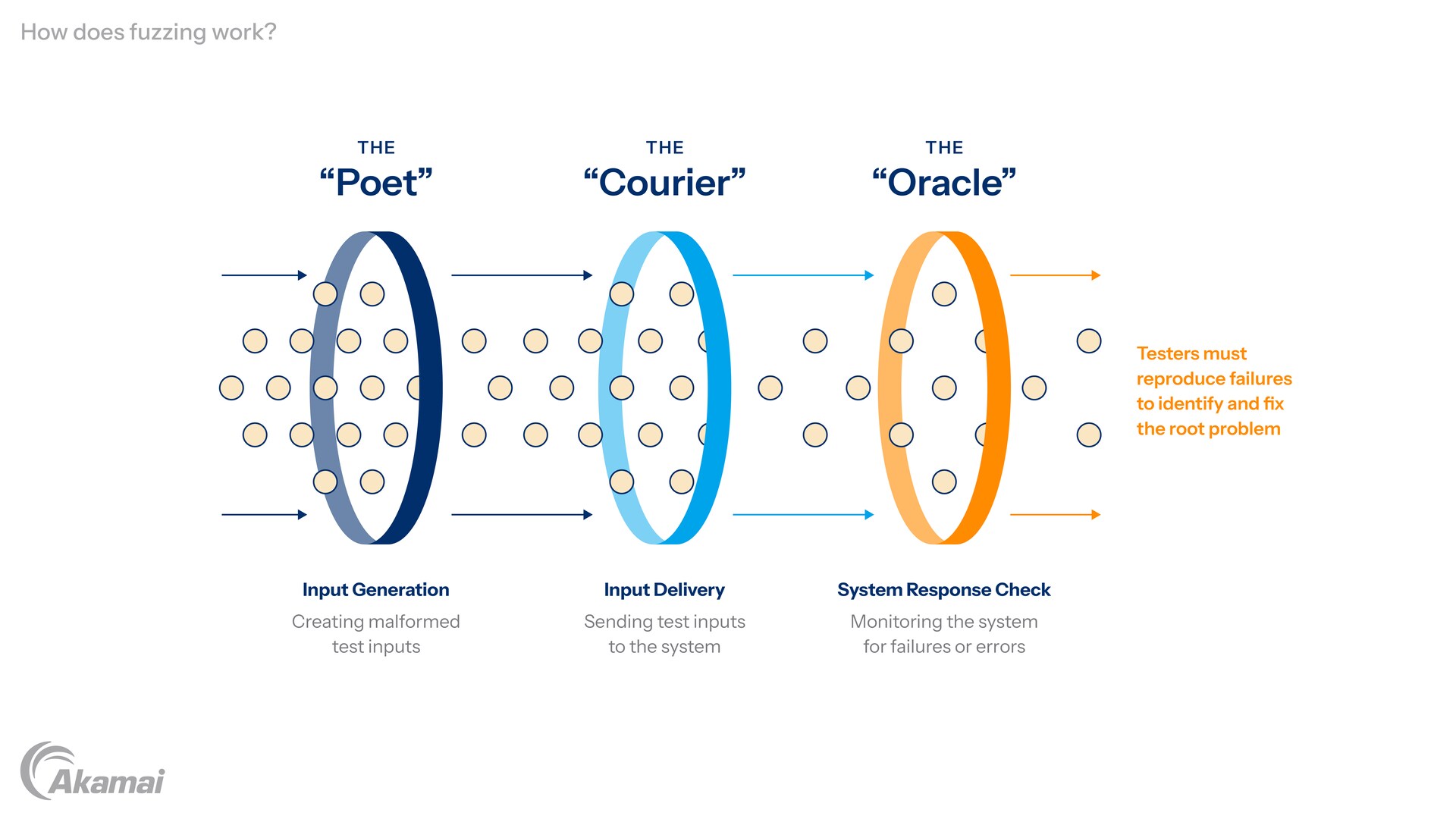
Fuzzing plays a crucial role in software development by enhancing security and reliability. It involves subjecting a software system to unexpected, invalid, or random inputs to identify vulnerabilities early in the development lifecycle. By simulating real-world scenarios and unexpected user inputs, fuzzing helps detect and address potential weaknesses, such as API vulnerabilities, before malicious actors can exploit them.
Incorporating API fuzz testing into the software development process promotes robustness and resilience, ultimately improving the overall security posture of applications. As a result, it’s an indispensable tool for ensuring the effectiveness of API security testing and mitigating potential risks.