Fast flux is a sophisticated technique used by cybercriminals to enhance the resilience and agility of their malicious infrastructure by rapidly changing the IP addresses associated with a domain name. This makes it difficult for security defenses to block or take down the infrastructure used in phishing and malware campaigns.
Introduction to Fast Flux
Cyberthreats are ubiquitous in today’s digital landscape. Phishing, in particular, is a prevalent method used by attackers to initiate larger and more complex cyber compromises. These attacks often start with the theft of logins, credit card numbers, or other valuable financial credentials. Malware, too, has become pervasive, infecting a wide range of devices, from personal computers and smartphones to Internet of Things (IoT) devices, to upload data or disrupt services.
Fast flux is a sophisticated technique employed by cybercriminals to enhance the resilience and agility of their malicious infrastructure. By rapidly changing the IP addresses associated with a domain name, fast flux makes it difficult for security defenses to block or take down the infrastructure used in phishing and malware campaigns. Most modern cyberthreats rely on the Domain Name System (DNS) to function effectively, and it plays a crucial role in facilitating fast flux operations, allowing attackers to maintain a moving target and evade detection.
The role of fast flux in cyberthreats
Fast flux can be connected to phishing and malware campaigns. Phishing attacks use DNS lookups to direct users to malicious websites or infrastructure set up to manage interactions with victims. Similarly, malware is programmed to “call home” using DNS lookups to obtain the IP addresses of command and control (C2) servers, where it can send status updates and receive instructions. To minimize the impact when these exploits are detected, developers of malicious software employ dynamic fast flux DNS resolution techniques.
Fast flux supports phishing campaigns and ransomware distribution by making it challenging for security teams to block or take down the infrastructure used in these attacks. By frequently changing the IP addresses associated with a domain, attackers can ensure that even if one IP address is blocked, others remain accessible. This resilience is further enhanced when fast flux is used in conjunction with botnets, which are networks of compromised devices controlled by a malicious actor. These botnets can be used to distribute malware and maintain a robust C2 network, making it harder for defenders to disrupt the attack.
Enhancing network security against fast flux attacks requires a multi-faceted approach. Security teams must implement real-time monitoring and analysis of DNS traffic to detect and respond to fast flux activities. This can be achieved through the use of advanced threat intelligence and machine learning algorithms that can identify patterns indicative of fast flux. Furthermore, collaboration with internet service providers (ISPs) and other service providers may be necessary to ensure a coordinated response to these threats.
How fast flux works
Fast flux networks operate by frequently changing the IP addresses of malicious resources in DNS responses for domain names. This rapid alteration ensures that if an IP address of a resource used to activate an exploit is blocked or taken down, other IP addresses for that resource remain accessible. The mechanics of fast flux networks are designed to obfuscate the real locations of malicious servers, making it difficult for security defenses to pinpoint and neutralize them.
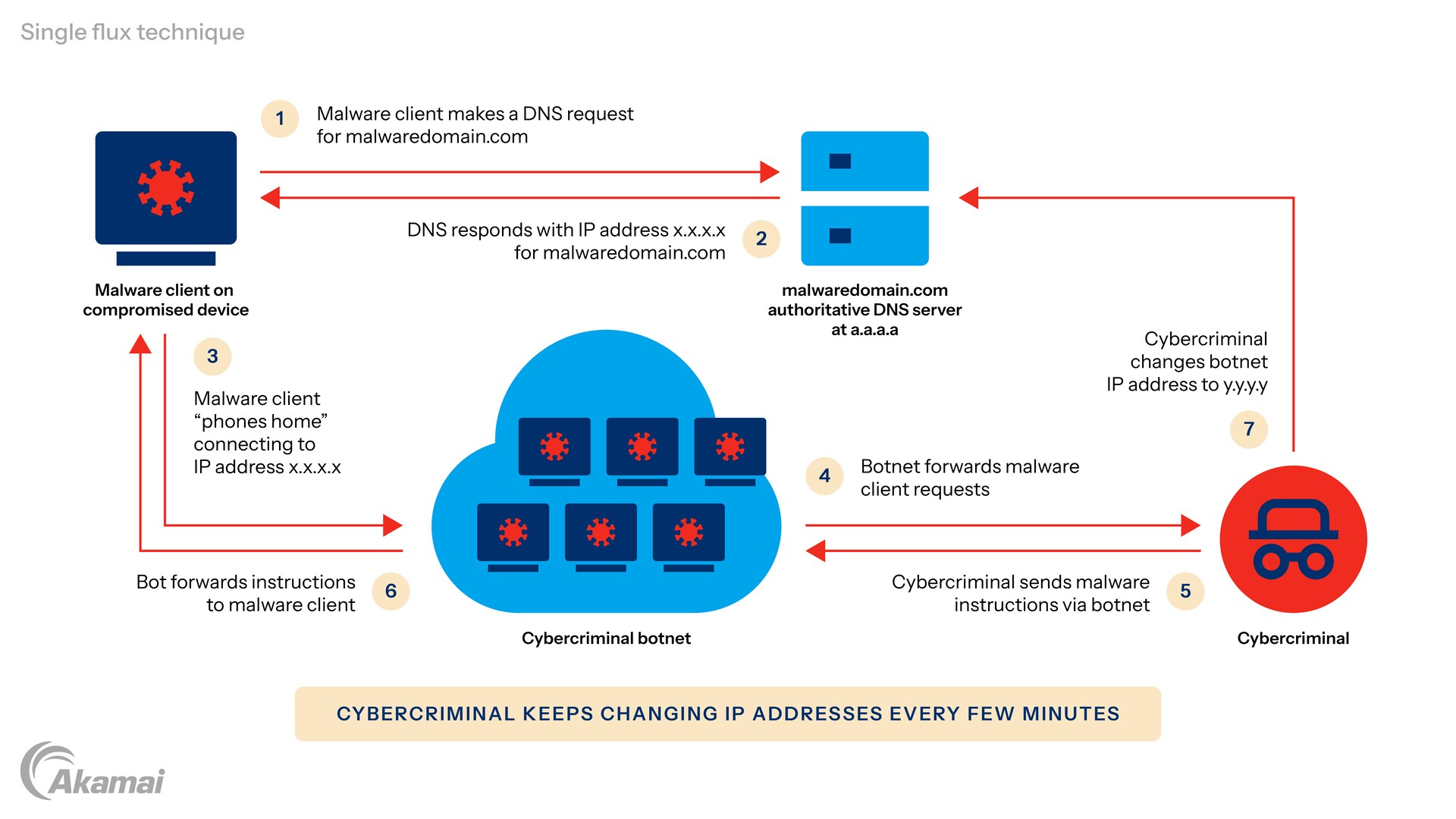
There are two common variants of fast flux: single flux and double flux. Single flux involves frequently changing IP addresses in DNS responses for a domain name. This ensures that even if one IP address is blocked, others remain available to sustain attacks. A related technique, domain fluxing, constantly changes domain names.
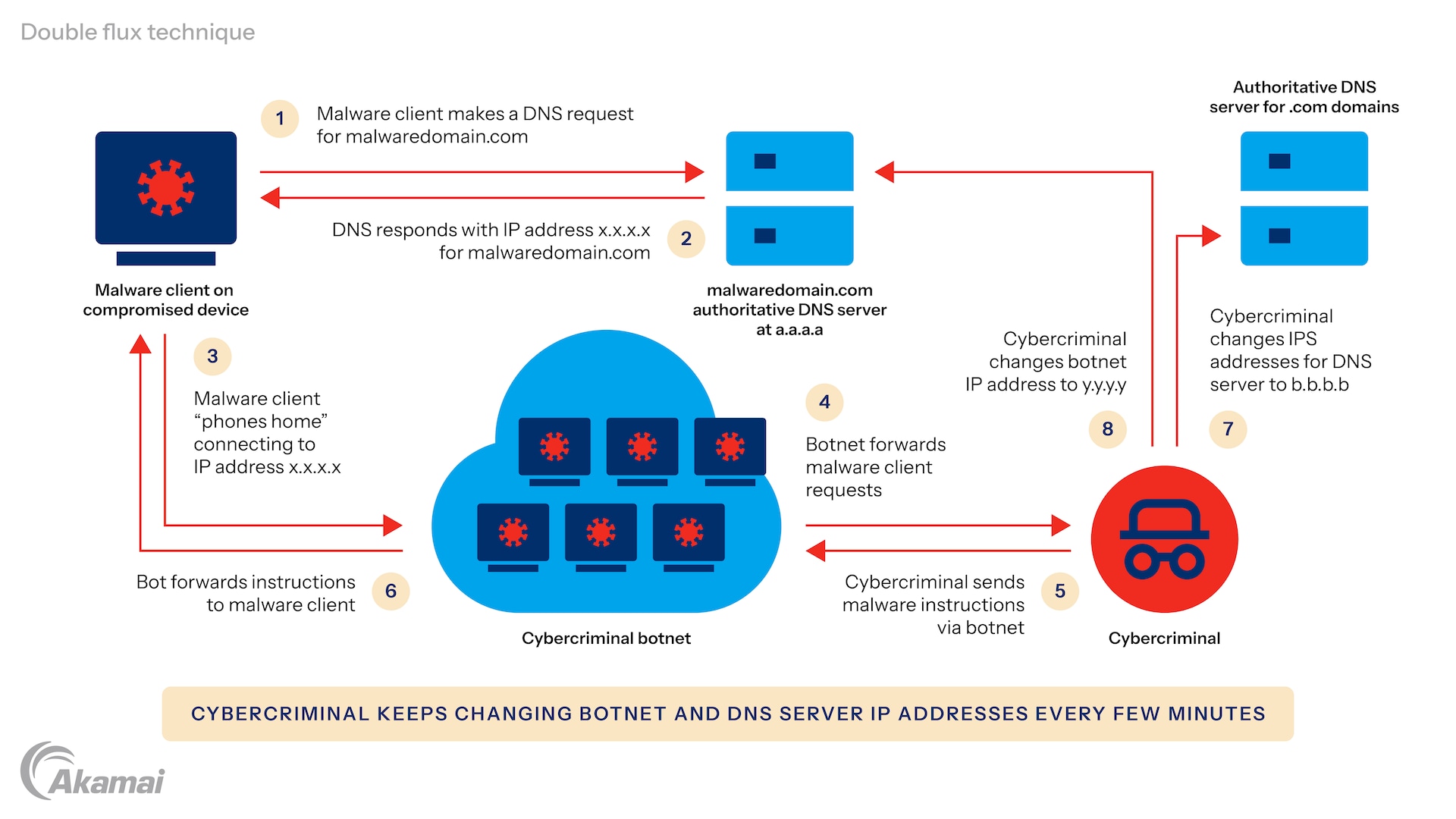
Double flux, on the other hand, not only changes the IP addresses of the resources used to activate exploits, but also frequently changes the IP addresses of the DNS nameservers responsible for resolving the domain names. This additional layer of resiliency and anonymity makes it even more challenging to disrupt the malicious infrastructure.
Domain fluxing is similar to fast flux. It involves using a domain generation algorithm (DGA) to programmatically generate new disposable domain names to support malicious activities. It also enables resilient and adaptive attacks and requires the parallel creation and deletion of DNS records associated with attack activity.
The dynamics of fast flux make it harder for some kinds of security measures to keep up, it’s a serious threat that multiple government agencies have recognized. In April 2025, the United States National Security Agency (NSA), Cybersecurity and Infrastructure Security Agency (CISA), and Federal Bureau of Investigation (FBI), along with the Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC), Canadian Centre for Cyber Security (CCCS), and New Zealand National Cyber Security Centre (NCSC-NZ), released a joint cybersecurity advisory.
The advisory warned businesses and organizations, ISPs, and security service providers of the ongoing threat of fast flux and the importance of implementing robust defenses.
What are mitigation strategies for fast flux?
Mitigating the risks associated with fast flux requires a comprehensive and proactive approach, spanning cybersecurity teams, threat intelligence deployed in network infrastructure, and potentially collaborating with other entities that touch your applications and networks — like ISPs, MSPs, and cloud services, described in more detail below.
DNS resolvers can be equipped with filtering mechanisms that use dynamic threat intelligence to track and block fast flux activity. IP-based threat intelligence can also be deployed in security firewalls to block or sinkhole addresses associated with malicious fast flux networks. Both DNS and IP-based threat intelligence require robust detection and validation analytics to avoid false positives and ensure the accuracy of the threat data.
Developers of threat intelligence use many techniques to quickly detect and properly mitigate fast flux attacks. Domain and IP reputation analysis, and correlation analysis, apply machine learning, AI, and other analytical methods to raw DNS query traffic gathered from resolvers and other third-party threat feeds, to identify domains and IPs associated with fast flux tactics and validate the activity is malicious. Analysis is typically done in real time, and fast flux domains are automatically incorporated into threat intelligence databases.
By deploying threat intelligence in network devices, security teams can then flag and block these domains and IPs to reduce the risk of successful attacks. This approach requires threat intelligence that is dynamic and accurate, with detection and validation analytics that match the speed and complexity of the threats they are designed to counter.
It’s necessary to note that some content delivery networks (CDNs) use techniques that resemble fast flux to maximize the reachability of their resources. These legitimate services must be allowlisted to avoid disrupting their operations.
Organizations with experienced resources can log and monitor their DNS traffic and other network communications to identify and track fast flux activities. Building in alerting mechanisms allows for rapid response to newly discovered fast flux domains and IP addresses. Proactive monitoring maintains a baseline of network security and minimizes the possibility that fast flux techniques can facilitate attacks.
Developing policies and procedures to manage and contain phishing incidents, particularly those facilitated by fast flux networks, is crucial for maintaining network security. These policies should include guidelines for identifying and reporting suspicious activity, as well as procedures for isolating and investigating potential fast flux domains.
Collaboration and information sharing are also critical components of a robust cybersecurity strategy. Organizations can participate in public and private forums to contribute their insights and maintain awareness of the latest findings. This approach helps to build a collective defense against fast flux and other advanced cyberthreats.
Coordinating with other entities that touch applications and networks — like ISPs, MSPs, and cloud services — may also be important. They need to be aware of the dangers posed by fast flux and implement defenses, like the ones described above, within their own networks.
Finally, coordination with legal entities may be necessary to combat fast flux threats. Law enforcement agencies, service providers, and target organizations can work together to take down fast flux networks and disrupt the operations of malicious actors. However, the challenges posed by bulletproof hosting services, which provide a haven for cybercriminals, can complicate these efforts. Bulletproof hosting (BPH) services are known for their resistance to takedown attempts, making it difficult to permanently neutralize fast flux networks.
Conclusion
Fast flux is a powerful tool in the hands of cybercriminals, enabling them to create resilient and adaptive attack infrastructures that are more difficult to disrupt. By understanding the mechanics of fast flux and implementing a comprehensive set of mitigation strategies, organizations can protect themselves against these sophisticated threats. Real-time monitoring, advanced threat intelligence, and collaboration with other organizations that touch your networks and applications (alongside collaboration with the cybersecurity community) are essential components of a robust defense against fast flux.
As the threat landscape continues to evolve, it is crucial for organizations to stay vigilant and proactive in their approach to cybersecurity. By combining technical measures with operational policies and regular awareness training, organizations can significantly reduce the risk of successful fast flux attacks and maintain the integrity and security of their networks. Akamai has a diverse portfolio of DNS security solutions to prevent data exposure, protect business systems, and cover connected workers with adaptive, agile, accurate DNS-based threat intelligence that deters fast flux. Learn more.
Frequently Asked Questions
Fast flux supports phishing and malware campaigns by making it challenging for security teams to block or take down the infrastructure used in these attacks. By frequently changing the IP addresses associated with a domain, attackers ensure that even if one IP address is blocked, others remain accessible, thus maintaining the continuity of their malicious activities.
The two common variants of fast flux are single flux and double flux. Single flux involves the frequent change of IP addresses in DNS responses for a domain name, while double flux changes both the IP addresses of the resources and the IP addresses of the DNS nameservers responsible for resolving the domain names, adding an extra layer of anonymity and resilience.
The TTL value in DNS records is set to a very low duration in fast flux attacks. Short TTLs make it harder for security defenses to track the true location of malicious servers so they aren’t detected and blocked.
Domain fluxing is another technique, similar to fast flux operations, that involves the rapid generation of new domain names to support malicious activities. These domains are often disposable and can be quickly abandoned if detected. Domain fluxing requires the parallel creation and deletion of DNS records associated with attack activity.
Mitigation strategies for fast flux attacks include advanced threat intelligence based on real-time analysis of diverse data sources using machine learning, AI, and other methods. It’s also important to collaborate with public and private security forums — and other organizations like ISPs, MSPs, and cloud services that touch corporate networks and applications — to contribute their insights and maintain awareness.
Machine learning and AI can analyze large volumes of data, such as DNS query traffic, to identify patterns and anomalies that may indicate the presence of fast flux. These technologies can quickly detect and properly mitigate fast flux attacks by incorporating insights into threat intelligence databases, helping security teams stay ahead of the evolving threat landscape.
Collaboration and information sharing are crucial in combating fast flux because they help build a collective defense against these sophisticated threats. By participating in public and private forums, organizations can contribute their insights and maintain awareness of the latest findings, which enhances the overall security posture and helps to identify and respond to fast flux activities more effectively.
Infrastructure used to enable exploits can take advantage of botnet command and control (C2) facilities to remain robust and resilient.
Organizations can ensure that legitimate services using techniques similar to fast flux, such as content delivery networks (CDNs), aren’t disrupted by carefully managing and allowlisting these services. Additional policies should be implemented to distinguish between legitimate and malicious fast flux activities, and to avoid false positives that could disrupt the operations of legitimate services.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.